Ethereum is preparing one of its most important security shifts to date, and it is not about faster block times or lower gas fees. The Ethereum Foundation is refocusing from speed to provable security, pushing zkEVM rollups toward a strict 128‑bit security standard by 2026 that could redraw the L2 landscape.
Over the last cycles, rollup marketing has revolved around TPS charts and “world’s fastest zkEVM” slogans. Ethereum researchers are now sending a different message: raw speed is meaningless if attackers can rewrite state because the underlying proofs rest on weak cryptographic assumptions.
What 128‑Bit Security Actually Means
In cryptography, “128‑bit security” roughly means that the best known attack would require around 21282^{128}2128 operations, which is effectively impossible with any realistic computing power. Each additional bit doubles the cost of breaking the scheme, so jumping from sub‑100‑bit to 128‑bit security is an exponential upgrade, not a minor tweak.
Regulators and standards bodies already treat 128‑bit as the baseline for long‑lived financial and government systems, including banking and hardware security. By aligning zkEVM proof systems with that bar, Ethereum is making a clear statement: serious value on mainnet must sit on quantifiable, institution‑grade cryptography.
Ethereum’s 2026 Roadmap for zkEVM Security
According to recent research updates, Ethereum’s roadmap sets 2026 as the target for zkEVMs that secure Ethereum L1 to meet 128‑bit provable security, measured by a common, public calculator. Before that, teams are expected to hit intermediate milestones such as solid 100‑bit security with practical proof sizes and verification times.
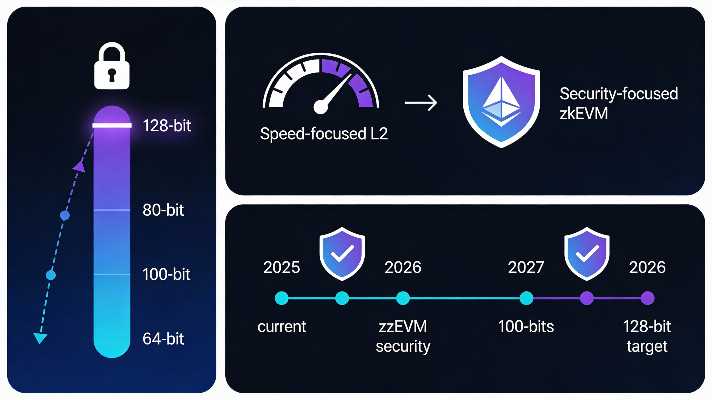
Instead of each project “grading its own homework,” the ecosystem is converging on a canonical tool (often referred to as a soundness or “soundcalc” calculator) to estimate bit‑security using shared assumptions and known attacks. This creates a common ruler for comparing proving systems and makes marketing claims much easier to audit.
New Cryptography: WHIR and Post‑Quantum Readiness
To reach 128‑bit security without exploding proof sizes, Ethereum researchers are exploring new primitives like WHIR, a Reed‑Solomon‑style proximity test that also acts as a multilinear polynomial commitment. WHIR is designed to be transparent, post‑quantum‑resistant, and more efficient than traditional FRI‑based constructions at the same security level.
Post‑quantum safety is not just a buzzword here. Long‑horizon capital such as banks, asset managers, and governments care about whether a system can remain secure for decades, even in the face of future quantum breakthroughs, and 128‑bit transparent proofs move Ethereum’s rollup stack closer to that requirement.
What This Means for L2s, DeFi and Institutions
For DeFi users, stronger proofs reduce the nightmare scenario where an attacker forges a “valid” proof, rewrites rollup state, and drains an entire L2 or bridge. A standardized 128‑bit bar significantly raises the cost of such attacks and makes risk assessment more concrete for power users and auditors.onesafe+1
For L2 teams, the new security standard becomes a filtering mechanism. Rollups that achieve verifiable 100‑bit to 128‑bit security with efficient proofs can market themselves as institution‑ready infrastructure for tokenized treasuries, compliant stablecoins, and regulated derivatives, while weaker systems risk being confined to speculative retail flows.
Institutions finally get a language they recognize. Instead of comparing TPS screenshots, they can ask: “Does this rollup meet 128‑bit security under the shared calculator, and is the proof system formally analyzed?”—a question that aligns Ethereum more closely with traditional cybersecurity and financial standards.





