Bitcoin
Bitcoin User Losses $16.2 Million in BTC After Using an Old Electrum Wallet

An anonymous Bitcoin user is claiming to have lost $16,000,000 (1400 Bitcoins) due to installing an old Electrum wallet version that is running malicious servers.
The user created an issue and explained what happened on the official Electrum’s github page.
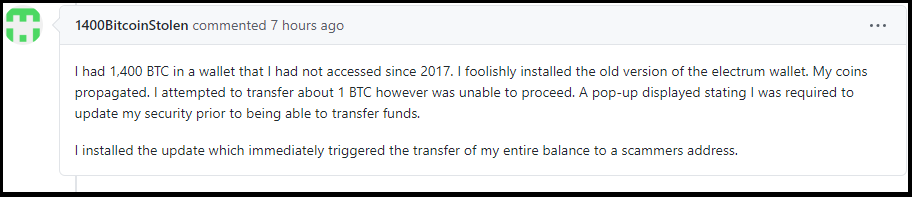
It seems the victim was using an infected version of Electrum wallet that asked him to install some sort of malicious updates that triggered the transfer of hist entire Bitcoin balance to a scammers address.
According to bitcoin blockchain the transfer of the stolen funds happened yesterday.
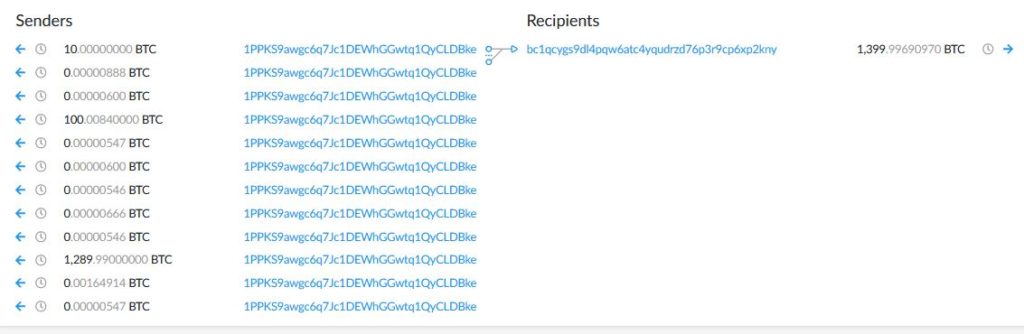
Electrum is a light client, which means it must connect to the blockchain through a server, which by default is chosen from a list of public Electrum servers. Anyone can operate such a public server and some users will be randomly connected to it.
When broadcasting a transaction on Electrum, it gets sent to the Electrum Server you are connected to for propagation to the network. The server should try to add the transaction to its mempool and further propagate it to other Bitcoin nodes.
it seems the attackers have set up a public Electrum Server targeting the old wallets’ users, which was tweaked so that instead of propagating the user’s transaction as it should, it always returns a malicious error message directing the Electrum clients to a phishing website to “upgrade” their Electrum version.
The only way to keep your Bitcoin and other digital currencies safe is to either use an offline wallet or a trusted hardware wallet.
Bitcoin
Telecom Giant Vodafone Bringing Crypto to the Masses Via SIM Cards

The major telecom company Vodafone has unveiled an ambitious plan to integrate cryptocurrency wallets directly into the SIM cards used by mobile phones on its network. This cutting-edge move aims to make blockchain technology and crypto easily accessible to millions of smartphone users worldwide.
What’s Happening?
Vodafone, one of the largest mobile operators based in the UK, intends to combine crypto wallets with the subscriber identity module (SIM) cards inside phones. SIM cards are little chips that allow mobile devices to connect to a carrier’s network.
By embedding a crypto wallet into these ubiquitous SIM cards, Vodafone wants to introduce blockchain and virtual currency technology to the masses through the smartphones we all use daily.
The Bigger Blockchain Picture
This crypto SIM integration is part of Vodafone’s bigger blockchain strategy. The company has developed its own “PairPoint Digital Asset Broker” platform to enable secure digital identities and transactions across different blockchains.
Vodafone’s blockchain lead David Palmer emphasized in an interview that mobile phones are the main way billions access digital services and commerce. So partnering blockchain with SIM card tech is crucial for widespread adoption.
By 2023, there will be over 8 billion mobile phones in use globally. And estimates suggest crypto wallets on smartphones could reach 5.6 billion by 2030 as digital money goes mainstream.
Financial Restructuring
The crypto wallet announcement comes as Vodafone seeks to restructure its finances and raise billions in new funds through debt offerings and loans over the next couple years.
The company plans to take on $2.9 billion in total debt, including $1.8 billion in direct loans. Some of this financial overhaul relates to issues at Vodafone’s Indian subsidiary Vodafone Idea Ltd.
While navigating these monetary hurdles, Vodafone still sees major opportunities in emerging technologies like blockchain and aims to be an innovator helping drive mainstream crypto adoption through the SIM card strategy.
Bitcoin
No Evidence of Hack, Says Bitfinex CTO Amid Ransomware Gang’s Allegations

In the world of cybersecurity, claims of data breaches can cause significant concern and speculation. Recently, a ransomware group named FSOCIETY claimed to have successfully hacked several organizations, including the cryptocurrency exchange Bitfinex. However, Bitfinex’s Chief Technology Officer (CTO), Paolo Ardoino, has dismissed these rumors, stating that a thorough analysis of their systems revealed no evidence of a breach.
According to Ardoino, who is also the CEO of Tether, less than 25% of the email addresses allegedly stolen from Bitfinex’s servers match legitimate users. This casts doubt on the validity of FSOCIETY’s claims regarding the supposed hack.
The ransomware group, styled after the fictional hacking group from the TV show “Mr. Robot,” claimed to have breached several victims, including Rutgers University, consulting firm SBC Global, and a cryptocurrency exchange they referred to as “Coinmoma,” which is likely a misspelling of Coinmama.
Ardoino expressed skepticism about the group’s claims, stating that if they had indeed hacked Bitfinex, they would have demanded a ransom through the exchange’s bug bounty program, customer support channels, emails, or social media accounts. However, Bitfinex received no such requests from FSOCIETY.
Furthermore, Ardoino shared a message from a security researcher suggesting that the real motivation behind the alleged hacks might be to promote FSOCIETY’s ransomware tools, which they reportedly sell access to in exchange for a subscription fee and a commission on stolen profits. Ardoino questioned the group’s need to sell their tools for $299 if they had truly hacked a major exchange like Bitfinex.
It’s worth noting that Bitfinex has previously fallen victim to a significant hack in 2016, resulting in the theft of a substantial amount of Bitcoin. Two individuals, including crypto rapper ‘Razzlekhan,’ pleaded guilty to money laundering charges in connection with that incident.
While the claims made by FSOCIETY have yet to be verified by the alleged victims, Bitfinex’s CTO remains firm in his stance that no breach has occurred. As cybersecurity threats continue to evolve, it is crucial for organizations to remain vigilant and take proactive measures to protect their systems and users’ data.
Bitcoin
Indian Police Seize 268 Bitcoins Worth $17 Million in Crypto Bust

Indian authorities have seized a large sum of bitcoins from a resident of Haldwani, a city in the northern Indian state of Uttarakhand. The seized cryptocurrency stash of 268 bitcoins is worth around $17 million at current prices.
The Enforcement Directorate (ED), a law enforcement agency that investigates financial crimes, carried out the bitcoin seizure. They arrested Parvinder Singh from his home in Haldwani after a raid prompted by information from US authorities.
Singh is allegedly part of an international drug trafficking syndicate called “The Singh Organization.” The criminal group used dark web marketplaces like Silk Road to sell drugs in the US, UK and other European countries.
To hide their illegal activities, the syndicate laundered the drùg money by converting it into bitcoins and other cryptocurrencies. ED officials said Singh and his associates received around 8,488 bitcoins over the years from their drùg sales on the dark web.
The bitcoin seizure was a rare collaboration between Indian and US law enforcement agencies. American officials have been investigating Singh and his accomplice Banmeet Singh for their roles in the international drùg cartel.
Cryptocurrencies like bitcoin are popular among criminals due to the anonymity they provide. However, this case shows authorities are getting better at tracing illegal crypto transactions and bringing the perpetrators to justice.
The investigation is still ongoing, and more arrests and seizures are expected as officials unravel the entire money laundering operation of The Singh Organization.
-

 Altcoins4 years ago
Altcoins4 years agoProject Review: Pi Network, a New Scam Project in Town
-

 Bitcoin4 years ago
Bitcoin4 years agoBitcoin Worth $1.2M Seized From Arrested Indian Hacker
-

 Altcoins5 years ago
Altcoins5 years agoReview: Play Arcade Games Inside ARK Wallet And Win Some Free Cryptocurrency
-

 Blockchain5 years ago
Blockchain5 years agoA Full Review: Utopia A New Decentralized P2P Blockchain
-

 Bitcoin5 years ago
Bitcoin5 years agoAnother Exit Scam: NovaChain Shuts Down
-

 Exchanges5 years ago
Exchanges5 years agoCrex24 Will Require KYC Verification
-

 Bitcoin5 years ago
Bitcoin5 years agoJohn McAfee Has Gone Missing
-

 Altcoins5 years ago
Altcoins5 years agoElrond Partners With ChainLink

















